News and Blogs
-
.png)
The Cyber Security Threats Lurking in Your Web Browser
Web browsers are essential for everyday use but can also expose you to cyber threats like phishing, session hijacking, and data theft. Learn about key security risks, how attackers exploit browser vulnerabilities, and best practices to protect your s... -
.png)
Ransomware Attacks: What to Do and What to Avoid
In the event of a ransomware attack, quick and calculated actions are vital to minimize damage. This guide offers essential steps on what to do and what to avoid during a ransomware attack, as well as effective prevention tips to safeguard your busin... -

What is The Difference Between Passwords and Passkeys
Discover the key differences between passwords and passkeys in our latest blog. Learn how these two authentication methods work, their strengths and weaknesses, and why passkeys are emerging as a more secure and user-friendly alternative... -
.png)
The A-Z Breakdown of IT and Cyber Security Abbreviations
The IT and cyber security world, like a lot of industries, is full of abbreviations. In this blog, we provide an A-Z breakdown of some widely used abbreviations to help explain some of the widely used terms.... -
.png)
Is My Business A Target for Cyber Criminals?
Frequently people ask us at LoughTec, "why would someone hack me, I am only a small or medium sized business?"... -

QUANTUM COMPUTING
Googles new quantum computing chip "WILLOW" has delivered almost incomprehensible performance !... -

Krispy Kreme Hacked
Krispy Kreme has reported a cybersecurity breach that disrupted its online operations in certain parts of the United States. The company cautioned that this incident could have a significant impact on its business.... -

BT Group Cyber Attack
BT Group has confirmed it is addressing an attempted cyberattack on one of its legacy business units following claims by the Black Basta ransomware group.... -
.png)
DELOITTE UK HACKED ?
Deloitte UK, one of the worlds big 4 accounting firms, who provide audit and assurance, tax, consulting and risk and financial advisory services to a broad cross-section of the largest corporations and governmental agencies have apparently been hacke... -
.png)
What is Malware?
Discover the key to understanding and defending against malware. This blog breaks down 12 types of malware, including viruses, ransomware, spyware, and cryptojacking, explaining how they operate, their potential impacts, and the steps you can take to... -
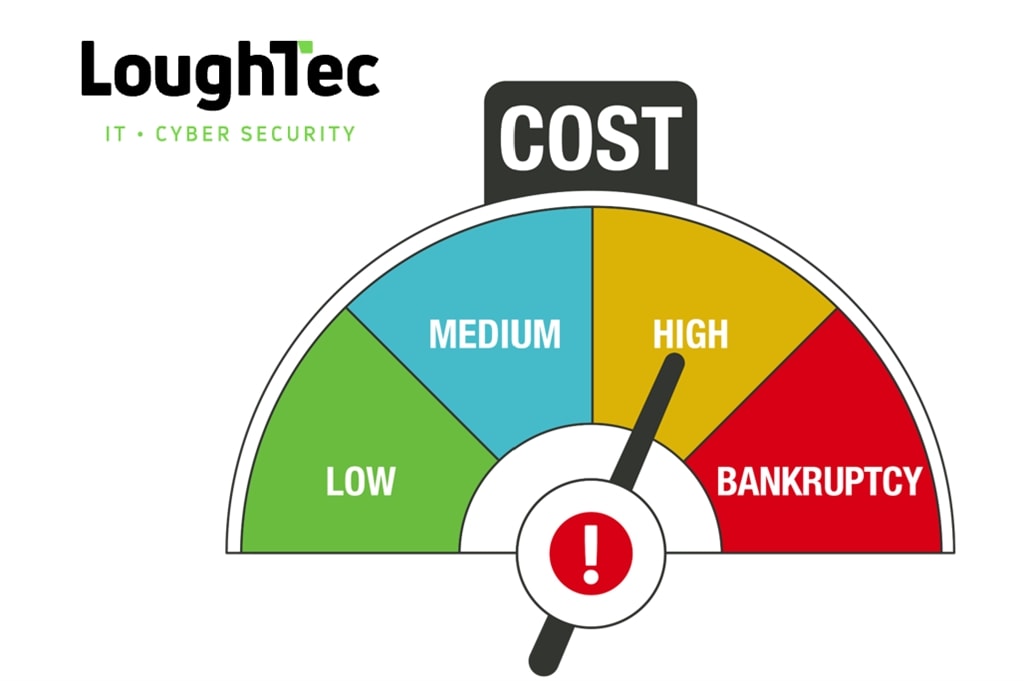
The cost of Cyberattacks in the UK
Cyberattacks cost U.K. businesses approximately 44 billion in lost revenue over the past five years... -

UK Hospital Cyber Attack
Wirral University Teaching Hospital confirmed that the ongoing issue at the Trust is expected to impact operations at Arrowe Park Hospital in Wirral.... -
.png)
WEBSITE RISK - Wordpress
Wordpress websites have two critical security flaws - urgently review if applicable !... -
.png)
Cyber Security - How to Stay Safe from Christmas Cyber Attacks
Christmas is coming soon and holiday periods are a perfect time for relaxing and connecting with family and friends however for the cyber criminals there is no holidays!... -
.png)
Password Security
Passwords are so widely used now and accepted as "business as usual" in both personal and business aspects that people know the associated high risk, as do businesses, however these are regularly overlooked in the importance of keeping a business cyb... -
.png)
CASIO Ransomware Attack
Japanese technology giant Casio said that the ransomware attack it suffered earlier this month has caused significant operational delay with no prospect of recovery yet.... -
.png)
How will AI increase the surface of cyber security attacks?
AI is poised to increase the cybersecurity attack surface in several key ways..... -

Deep Fake Scam
A finance worker is victim to a sophisticated deepfake scam, resulting in a loss of $25 million.... -

Railways Wi-Fi Cyber Attack
Cyber vandalism incident at 19 UK railway stations... -

World Record Ransom Payment
Breaking a world record is usually associated with a fantastic achievement, but not in this case....... -

Data Centers are now Critical Infrastructure
Data centres in the UK are to be classified as critical national infrastructure now.....
News & Blogs | IT & Cybersecurity Insights Northern Ireland
Welcome to the LoughTec News and Blogs hub, your go-to destination for the latest thinking, insights and commentary on cybersecurity Northern Ireland, IT managed services NI, and broader technology trends shaping businesses today. As a leading provider of managed IT and cybersecurity services across Northern Ireland, Ireland and the UK, LoughTec shares practical advice, industry analysis and future-proof strategies to help organisations stay ahead of modern threats and operational disruptions.
Why Our News & Blog Content Matters
In an era of rapidly evolving technology, regulatory change and cyber-threat complexity, staying informed is no longer optional – it is essential. Our blog posts and news articles surface real-world challenges, innovation in IT management, and emerging risks facing businesses in Northern Ireland and beyond. Whether you are responsible for IT infrastructure, cybersecurity operations or business continuity planning, our curated content keeps you up to date, supports your decision-making and strengthens your competitive advantage.
Explore topics such as:
- The rise of ransomware and supply-chain attacks and their implications for Northern Irish companies
- How remote and hybrid working has increased vulnerability in IT support and security models
- Best practices for deploying IT managed services Northern Ireland, reducing downtime and enabling scalability
- Emerging cyber-security frameworks, compliance obligations and what cybersecurity means for boards and executives
- Cloud transformation, infrastructure modernisation, and how IT operations can align with business growth
Thought Leadership for IT & Cyber Professionals
At LoughTec, our experienced team of consultants, analysts and technical experts contribute directly to our news and blogs. Each article is grounded in hands-on experience with clients, real incidents, and current threat intelligence from our 24/7 Security Operations Centre (SOC). This means readers not only gain theory, but actionable insight.
For example, our recent exploration of shadow-IT risk revealed how local NI teams circumvent formal IT processes, creating blind spots for cyber defenders. We analyse how to detect these behaviours, build governance frameworks and integrate with IT managed services to reduce risk. Similarly, our commentary on multi-factor authentication bypass attempts offers practical steps for IT leadership to harden access control and protect data.
Tailored for the Northern Ireland Market & Beyond
While many IT and cyber blogs offer generic advice, ours is specifically aligned to the Northern Ireland, Irish and UK market. We understand the regulatory, cultural and operational factors facing organisations in Northern Ireland, from SMEs to enterprises.
Many articles focus on how IT managed services can integrate with local business needs, how cybersecurity can address region-specific threats, and how companies can leverage local expertise to bolster resilience. Our content also spans sectors including manufacturing, healthcare, education, financial services and public sector. By offering sector-specific posts, we empower business leaders and IT professionals to benchmark best practice, mitigate threats and optimise operations.
Regular Updates to Stay Ahead
We publish on a consistent schedule, covering breaking security stories, deep-dive technical features and opinion pieces on strategy, compliance and emerging technology. By subscribing to our blog or visiting the news page regularly, you’ll always be first to hear about:
- Threat intelligence from our SOC and how it impacts NI businesses
- IT operations best practices to support growth and digital transformation
- New regulations, standards and what they mean for your cybersecurity posture
- Practical how-tos, checklists and tool recommendations for IT support teams
Join the Conversation & Take Action
Beyond reading, we encourage you to engage, follow us on LinkedIn, like and comment on posts, share insights and connect with the LoughTec team if you’d like to learn how we can support your organisation. Our content often links directly to services such as managed IT support Northern Ireland, vulnerability testing, cyber-risk assessments and fully managed security solutions, ensuring you’re informed and empowered to act.
Explore the latest articles in our News & Blogs section and stay ahead of technology, threats and operational demands. As your local Northern Ireland partner in cybersecurity NI and IT managed services NI, LoughTec is committed to helping your business secure its future.






